Comprehensive Guide To VPN: Internet Security 101
In this modern digital age, most of our time is increasingly spent online. While it has provided us with greater convenience and better connectedness, the internet has also become a hotspot for cyber risks that threaten our privacy and security.
Fortunately, numerous security tools have become readily available to help the average user to stay protected when browsing online. And one of the preferred security tools today is VPN.
What is a VPN?
A VPN, short for Virtual Private Network, is a service that safeguards your internet connection and online activities. It establishes an encrypted and secure connection between your device and the internet.
To help you understand better, here’s a scenario to visualize:
imagine the internet as a highway you travel to on motorcycles. Riding a motorcycle on an open highway road, you’re totally visible. Anyone can follow you, see who you are, where you go, and your activities. In short, you’re traceable.
Now, think of a VPN as a heavily-tinted car traveling a private tunnel instead of an open road. It acts as your personal tunnel that encircles you, concealing you and blocking anyone from tracking you.
In short, a VPN can hide your IP address and encrypt your online connection.
What Does a VPN do?
A VPN service can do a lot of things. Below there is a quick rundown of some of the things you can do with a VPN service.
Bypass Censorship
Some countries and governments block access to certain services and websites for their residents. A VPN can change your virtual location, which allows you to bypass censorship and access restricted content in other parts of the world.
Stop Online Tracking
VPNs can provide an encrypted tunnel that blocks your ISP and other websites from tracking data, including your geographical location, IP address, and browser metadata.
Unblock Streaming Platforms
This is one of the most common use cases of a VPN service. Most streaming platforms or streaming content are only available in specific locations. A VPN allows you to access these restricted platforms and content worldwide.
Access To Private Networks
A VPN can also be used to connect to a private network remotely. While you may still use the internet, a VPN can provide a barrier between the private network and the open web.
Note that a VPN can hide and change your IP address and remove accountability. As a result, some people may also use it for torrenting copyrighted content and engaging in other illegal online activities.
Why use a VPN?
By now, you should better understand what a VPN is and what it can do. Next, let’s look at the ‘why’ of VPNs.
Public Wi-Fi Security
People have become reliant on the internet more than ever- we want to stay connected and online every minute. While you can always connect to the web via mobile data, free public Wi-Fi can be pretty convenient. However, connecting to your favorite coffee shop’s Wi-Fi may cause security issues.
When you’re absent-mindedly scrolling through your social media at a local coffee shop or answering emails at the airport, malicious entities may be tracking your online activity.
Using a VPN lets you protect your data while you’re on other networks, hiding your account passwords, banking information, and browsing history from internet strangers.
Data Privacy And Security
Even if you don’t use a public Wi-Fi network, you may still be vulnerable with your home or private network. With a VPN service, you can protect your data privacy against your internet service provider, the apps, websites, and services you use, and even the government.
A VPN can help conceal your IP address, limiting the collection of your location, browser history, and other online activities.
Boost Your Security
While a VPN is not an all-rounder security tool, it does help in boosting your online security. In fact, a reliable VPN service can help protect you against several security breaches, including rogue Wi-Fi networks, packet sniffing, man-in-the-middle attacks, and more.
Access Geo-Restricted Content
One of the primary reasons why people utilize VPNs is to access region-blocked websites and content. Most popular streaming services limit their content depending on which country you access the site from. Thus, you may not be able to watch your favorite TV show or movie.
However, a VPN can help change your IP address and make it look like you’re accessing the site in an unrestricted country. This allows you to view content that may not be available in your location.
In addition, you may also use VPN to break through firewalls on office or school networks so you can access restricted sites such as social media sites.
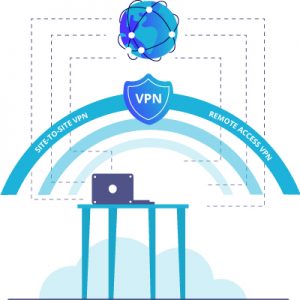
Types of VPN
In general, VPN can be categorized into two types:
Remote Access VPN
Remote access VPNs are typical consumer-grade VPNs. It’s what you think of when talking about VPNs.
A remote access VPN allows you to securely connect to a private network, such as an office network. It allows you to safely use and access applications and data over the internet, encrypting all traffic that the user receives and sends.
Site-To-Site VPN
Unlike a remote access VPN, where an individual can connect to a network and use its resources, a site-to-site VPN joins two or more networks from different sites. This type of VPN is further divided into two categories:
Intranet-Based Site-To-Site VPN
An intranet-based site-to-site VPN refers to multiple connected local area networks (LANs) to form a wide area network (WAN). A company may also use this type of setup to incorporate a software-defined WAN (SD-WAN).
This type of VPN is helpful in securely combining and pooling resources across a company with multiple offices as if they were all in the exact physical location.
Extranet-Based Site-To-Site VPN
Unlike an intranet-based VPN, an extranet-based site-to-site VPN is commonly used between partner companies. It allows them to share specific information externally while maintaining security. It also allows internal networks to be used only by their internal employees.
In short, an extranet-based site-to-site VPN can help two different companies share specific resources but still keep others private. It allows each entity to choose what they want to share with the other company and vice versa to collaborate without exposing critical data.
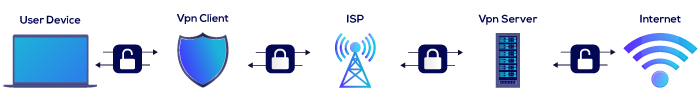
How Does a VPN work?
VPNs work by using encryption protocols to funnel all internet traffic via an encrypted tunnel between a remote VPN server and your computer. It conceals your IP address and secures your data to prevent other entities from intercepting it.
To explain it further, we share three steps and mechanisms on how a VPN secures your internet connection and overcomes the limits of an unsecured Wi-Fi.
Tunneling
First off, a VPN uses tunneling mechanisms that create a secure tunnel between two entities. Technically speaking, there’s no actual tunnel but just a logical link across the IP networks. These two ends of the tunnel, which are distant and only connected via multiple intermediate nodes, become virtually end-to-end connected during the logic process.
Think of it like this:
The data packets arrive at the tunnel entrance. There, it is further encapsulated by the tunneling protocol. Then, it is sent on the network to the tunnel exit. The encapsulation is removed when reaching the destination.
Authentication
Depending on the type of protocol used, the authentication process helps authorize access, guarantee non-rejection and ensure secure transmission.
What happens during authentication is as follows:
A client contacts the server and requests it to be identified. The server notifies a client’s presence and verifies if the connection attempt is authorized via authentication. When successful authentication occurs, the server authorizes communication with the client. The communication starts between the client and the server.
Encryption
Encryption or also referred to as cryptography is the technique that ensures data security and confidentiality by transforming it into encoded data that’s incoherent to unauthorized individuals. Once it reaches its destination, a decryption function reverses the process.
The type of encryption used mainly depends on the protocol used by your VPN provider. That said, encryption algorithms can be classified into three types:
Hashing: This uses a non-reversible or unique hash function to secure data.
Asymmetric: It uses a different key to encrypt and decrypt data.
Symmetric: The opposite of asymmetric, symmetric uses the same key for encryption and decryption.
VPN Protocols
A VPN protocol determines how information and data is routed through an internet connection. Different protocols have different specialties, depending on the desired requirements and user needs. The most commonly used VPN protocols include:
PPTP
Short for point-to-point tunneling protocol, PPTP is one of the oldest participants in the world of protocols. In fact, it’s been around since Windows 95. Unfortunately, it relies on an outdated authentication suite, the MS-CHAP v2, making it easy to crack.
That said, it does come with an advantage. The lack of authentication and encryption means that it is one of the fastest VPN protocols.
SSTP
SSTP, or secure socket tunneling protocol, was developed by Microsoft. It was introduced along with Windows Vista. It is pretty similar to a PPTP tunnel but wrapped in SSL, an encryption protocol for securing web pages.
SSTP worked only on Windows devices and never gained popularity other than that. Plus, it has limited configurability and flexibility and doesn’t stand out against other protocols.
L2TP/IPSec
A significant upgrade from pioneering protocols like SSTP and PPTP, the layer 2 tunneling protocol or L2TP delivers better security but compromises speed. In addition, L2TP alone doesn’t offer any authentication or encryption. Simply put, it’s a VPN tunneling protocol that creates a connection between you and the VPN server.
Thus, it is often paired with other tools in the Internet Protocol Security or IPSec suite to encrypt your traffic to keep it secure and private by encrypting and authenticating each individual IP packet.
The combination of these two is referred to as L2TP/IPSec. An L2TP/IPSec is generally more suitable for anonymity than security.
IKEv2
Internet Key Exchange Version 2, or IKEv2 in short, is one of the newbies in the world of VPN protocols. It comes with significant strength, primarily speed. Also, it’s suitable for mobile users across all platforms.
That said, IKEv2 is primarily used in a corporate environment. However, it doesn’t have native Linux support and lacks configurability. Plus, IKEv2 is also difficult to audit because of its strict licensing. IKEv2 is a popular choice by most popular VPN providers and is often used when you set ‘automatic’ on most VPN apps.
OpenVPN
A highly configurable open-source protocol, OpenVPN is available freely for all platforms and is highly regarded by the security community. This makes it widely adopted among consumer VPN providers.
An OpenVPN protocol can easily be configured to mask itself as regular internet traffic, allowing it to evade detection by firewalls and filters. In addition, this protocol has been widely reviewed and audited by reliable, independent researchers. Thus, it is tested and suitable for deployment in sensitive environments.
OpenVPN runs on either the UDP or TCP internet protocol. The latter guarantees that your data is delivered entirely in the correct order, while the former focuses on faster speeds. In general, most VPN providers using this protocol will allow you to choose between TCP or UDP.
SoftEther
SoftEther is a multi-protocol, open-source VPN client and server software. It’s relatively new compared to WireGuard, and yet it quickly gained popularity thanks to its speed, security, and stability.
It features advanced functionality such as Remote Procedure Calls (RPC) over Hypertext Transport Protocol (HTTPS) and GUI Management. SoftEther is considered faster than OpenVPN and also uses the same security tools. Plus, it works with most operating systems, such as FreeBSD and Solaris.
Unfortunately, SoftEther is not as tested and used as OpenVPN, which has been here for years already.
WireGuard
WireGuard is a newcomer in the protocol landscape, yet it has become a hot option in the VPN industry. This is a free, open-source VPN protocol written by Jason Donenfeld. WireGuard has shown its potential as a modern VPN protocol and offers speed with its lighter codebase. That said, it uses state-of-the-art encryption and cryptography that outperforms current leaders like IKEv2 and OpenVPN.
This resulted in several VPN providers adopting WireGuard in the past years. However, please take note that because it’s still in its experimental stage, VPN providers need to consider new solutions to overcome its vulnerabilities. Plus, it is also lagging behind cross-platform compatibility.
Disadvantages of VPN
While VPNs are a reliable way to ensure online privacy and security, it’s essential to understand that they does have their own limitations and disadvantages. Below, we’re sharing some of the downsides of using a VPN.
It Won’t Provide You Full Anonymity
Even top-notch VPNs can’t guarantee your anonymity. Your browsing activity can still reveal your identity in ways that a VPN service can’t control. For instance, if you’re logged into your Facebook account, your VPN provider can’t stop these companies from monitoring your activities.
In addition, web trackers and cookies store details about you that can be used to identify you even with a VPN connection.
VPNs Can Slow Down Your Internet Connections
Using a VPN service may slow down your internet connection. Your connection takes a longer route to the internet and runs first to your chosen VPN server.
With reliable VPNs, the speed loss is unnoticeable. However, you’ll experience slow download speeds and increased latency for poor-quality VPNs. This can be quite problematic if your internet connection is already slow or you’re doing speed-sensitive activities such as gaming or streaming.
Your Privacy Isn’t Always Guaranteed
VPNs can prevent unwanted individuals from monitoring your online activity. However, using a VPN service also means handing your browsing activity over to your VPN provider. They could see who you are and your online activities if they wanted to. Your privacy is dependent on how trustworthy your VPN provider is.
It Won’t Protect You Against Phishing And Malware Attacks
Not knowing the limits of VPNs can result in the false impression that you’re ‘invincible’ online. High-quality VPNs can protect you from man-in-the-middle and eavesdropping attacks. However, it’s not a comprehensive cybersecurity tool that can save you against every cyber-attacks.
A standalone VPN can’t secure your device against most forms of malware such as spyware, ransomware, and viruses. Also, it doesn’t protect you against social engineering attacks or phishing scams. After all, phishing scams occur when you click on malicious links and download malicious files to your device.
However, note that some VPN providers do offer extra features such as anti-malware software, adblocker, and other security tools.
VPNs Are Illegal In Some Nations
Using VPN is legal in most countries. However, a few nations restrict or ban the use of VPNs. These countries include North Korea, China, United Arab Emirates, Russia, Belarus, Iran, etc.
Therefore, you could be breaking the law by using a VPN and be prosecuted if caught.
Other than that, using VPN to perform illegal activities is still illegal regardless of where you are. And you could face charges when caught.
Some Online Services May Ban VPN Users
Some online services discourage VPN use or even prohibit its use entirely. This is particularly true for streaming services like Netflix, which block VPNs to stop users from accessing movies and videos that are not licensed in your location.
While it’s not illegal to use VPNs to unblock restricted content, it may be against a company’s terms of use. The company has the right to delete or suspend your account if you’re found using VPN to access restricted content.
FAQ
How to choose a VPN?
Which VPN to choose?
When to use it?
Is a VPN Legal?
Is it Safe?
Do I need a VPN for mobile?
Are Free VPNs safe?
When I use a VPN, Can I be tracked by Police?
What are the most popular VPN companies?
Is It difficult to set up a VPN?
How To Tell If An IP Is A VPN?
Does a VPN Hide History?
VPN Guides
Check our articles and reviews related to VPN below.